Thus, public key digital signatures provide authentication and knowledge integrity. A digital signature also offers non-repudiation, which signifies that it prevents the sender from claiming that he or she did not truly send the information. These options are each bit as basic to cryptography as privacy, if not more. Asymmetric key cryptography, or public key encryption, is usually thought of a more secure method to defend sensitive information. Asymmetric encryption entails using two keys – a private and a public one – to encrypt and decrypt information. Both keys are related — you need one to encrypt info and the opposite to decrypt it.
Anyone else who by some means gets their hands on this piece of information shouldn’t be capable of perceive it. The most necessary precept to maintain in mind is that you should never attempt to design your individual cryptosystem. The world’s most good cryptographers (including Phil Zimmerman and Ron Rivest) routinely create cryptosystems with serious safety flaws in them. In order for a cryptosystem to be deemed “secure,” it should face intense scrutiny from the safety community. Never depend on safety by way of obscurity, or the fact that attackers could not have knowledge of your system. Remember that malicious insiders and determined attackers will try and attack your system.

You might recognize some of these principles from variations of the CIA triad. The first of those makes use of is the apparent one—you can keep information secret by encrypting it. The others take a bit of explanation, which we’ll get into as we describe the different types of cryptography. Most people are acquainted with proscribing access to pc systems by way of a password, which is a novel string of characters that a person sorts in as an identification code. In a PKI surroundings, communication of revoked certificates is mostly achieved via a data construction referred to as a Certificate Revocation List, or CRL, which is revealed by the CA. The CRL contains a time-stamped, validated listing of all revoked, unexpired certificates in the system.
Why Is Cryptography Important?
It entails using complex mathematical algorithms to rework the unique data (i.e., plaintext) right into a format generally identified as ciphertext. Unlike symmetric and asymmetric encryption, hashing is a one-way process. You can produce a novel hash for enter data, however decoding the information behind a hash worth is unimaginable. That stated, some hackers may launch brute-force and dictionary assaults to see if they’ll produce the identical hash worth for input. That’s why it’s necessary to make use of sturdy cryptographic hash functions (and even further measures like password salting).
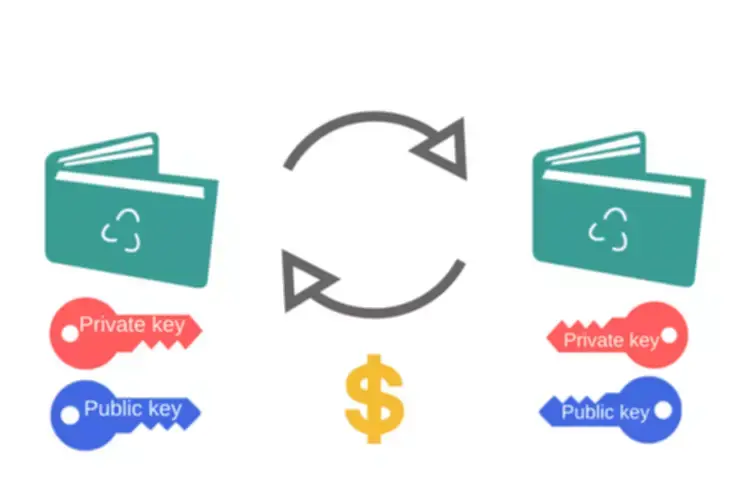
Therefore, cryptography performs an important role in cyber security by defending confidential data from unauthorized access and verifying its authenticity for safe communication between events on-line. The major advantage of public key cryptography is that it allows individuals who don’t have any preexisting security arrangement to change messages securely. The need for sender and receiver to share secret keys through some safe channel is eliminated; all communications involve only public keys, and no private secret is ever transmitted or shared. Cryptography began with ciphers, the primary of which was the Caesar Cipher. Ciphers had been lots simpler to unravel in comparison with fashionable cryptographic algorithms, but they both used keys and plaintext. Though easy, ciphers from the past have been the earliest forms of encryption.
Cryptography is using mathematical ideas and rules to secure data and communications. Derived from the Greek word kryptos, which suggests hidden, the definition of cryptography refers to changing intelligible textual content into unintelligible text, and vice versa. Cryptographic techniques allow only a message’s sender and meant recipient to read the decoded contents. Your non-public key’s encrypted in your disk utilizing a hash of your passphrase as the secret key. A passphrase ought to be exhausting so that you just can overlook and difficult for others to guess.
Manual Key Administration Processes
It is computationally infeasible to deduce the personal key from the public key. Anyone who has a public key can encrypt data however cannot decrypt it. Only the one who has the corresponding personal key can decrypt the data. Blowfish, a symmetric block cipher, is often used for file encryption. You’ll typically find it as one of the security measures in file storage and encryption software program designed to guard files from unauthorized access. With everybody constantly exchanging info on-line, guaranteeing knowledge authenticity, integrity, and confidentiality is paramount.
Revoked certificates stay on the listing only until they expire, then they’re removed from the list — this keeps the record from getting too lengthy. Only the certificate’s owner (the holder of its corresponding non-public key) or somebody whom the certificates’s owner has designated as a revoker can revoke a OpenPGP certificate. Expired certificates are unusable, however don’t carry the same threat of compromise as a revoked certificate. OpenPGP requires one Completely trusted signature or two Marginally trusted signatures to determine a key as legitimate. OpenPGP’s method of contemplating two Marginals equal to 1 Complete is much like a merchant asking for 2 types of ID. You might contemplate Alice pretty trustworthy and in addition contemplate Bob pretty reliable.
Cryptography
The West Virginia University Health System (WVUHS) accommodates a quantity of establishment areas, hospitals, and clinics. Welltok is a communications platform that enables patients and physicians to talk whereas encouraging wholesome how does cryptography work life. LoanCare is a sub-servicing entity that assists mortgage loan suppliers with finance and knowledge capabilities; they service over 1.5 million prospects across the states and beyond.
- The Diffie-Hellman algorithm was devised in 1976 by Stanford University professor Martin Hellman and his graduate pupil Whitfield Diffie, who are thought-about to be liable for introducing PKC as an idea.
- In this highly digital age, it’s close to unimaginable to erase all info online about your self, but you are capable of do so much to take away on-line info and minimize your threat of identification theft or worse.
- Public-key encryption puts him out of business (probably to his relief).
- Revoked certificates stay on the listing solely until they expire, then they’re removed from the list — this retains the list from getting too long.
- So he replaced every A in his messages with a D, each B with an E, and so on via the alphabet.
- Attackers can bypass cryptography, hack into computers which may be answerable for data encryption and decryption, and exploit weak implementations, such as the use of default keys.
Cryptographic strength is measured within the time and sources it might require to get well the plaintext. The result of strong cryptography is ciphertext that may be very difficult to decipher with out possession of the appropriate decoding software. Given all of right now’s computing power and obtainable time — even a billion computers doing a billion checks a second — it’s not attainable to decipher the outcomes of strong cryptography earlier than the tip of the universe.
What’s E Mail Spoofing, And How Can You Shield Yourself?
Cryptography is used to maintain messages and knowledge safe from being accessible to anyone apart from the sender and the meant recipient. Cryptography often makes use of encryption and an algorithm to maintain digital data and messages secure and only readable by the meant events. The term itself comes from the Greek word kryptos, which translates to hidden. Today, cryptography is predicated on laptop science practices and mathematical principle. The computations wanted for uneven cryptography are much more complex and resource intensive that those behind symmetric infrastructure. Fortunately, you don’t want to use it to protect every message you send on-line.
In the image below, you see the process of utilizing both symmetric and uneven encryption to switch information and secret keys privately. Make positive that you solely use algorithms, key strengths, and modes of operation that conform to industry best practices. Advanced encryption standard (AES) (with 128, 192, or 256-bit keys) is the usual for symmetric encryption. RSA and elliptical curve cryptography (ECC) with no less than 2048-bit keys are the standard for asymmetric encryption.
Here, you are going to use the software program called Wireshark, which helps in analyzing network traffic from your system, so you possibly can see what kind of information enters and leaves the machine. A cryptosystem supplies for managing cryptographic keys together with era, change, storage, use, revocation, and alternative of the keys. In such a case it is clever to split the key among multiple folks in such a means that a couple of or two folks should current a bit of the key so as to reconstitute it to a usable situation.
In current occasions, cryptography has was a battleground of a few of the world’s greatest mathematicians and computer scientists. The capacity to securely retailer and switch delicate info has proved a critical consider success in war and enterprise. As you presumably can see, there is a bunch of gibberish data here that reveals nothing you searched or learn. Similarly, other secured web sites operate this fashion and it’s very troublesome if at all attainable, to listen in on consumer information. Now you will undergo how modern-day cryptography has helped in preserving the info secure on the web with an illustration of what is cryptography.

Modern cryptography methods embody algorithms and ciphers that allow the encryption and decryption of data, such as 128-bit and 256-bit encryption keys. Modern ciphers, such because the Advanced Encryption Standard (AES), are thought of nearly unbreakable. The use of cryptography can be traced to the ancient Egyptians and their creative use of hieroglyphics. The receiver must already possess the non-public key generated from the identical pair.